This post is about the paper A polynomial time attack on instances of M-SIDH and FESTA by Wouter Castryck and Frederik Vercauteren.
As we all know, SIDH was broken in 2022 by using knowledge of exact images of torsion points under a secret isogeny. (For more details, see previous blog post, and another, and Quanta article.) Precisely, in SIDH the secret isogeny has known degree
, and one is given
where
are a basis for
. Here
The key technique is a result from Kani, which involves isogenies of Abelian varieties of dimension more than one.
In response, several papers proposed ways to fix it by “blinding” the images of the torsion points and/or the degree of the isogeny . The M-SIDH paper proposed to hide the degree of
and to blind the points as
for some secret
that squares to one modulo
. FESTA is a bit more general, and I won’t talk about it in detail here.
Sections 4.2 and 4.3 of the M-SIDH paper show an attack on the scheme for special curves using “lollipop” maps (see below). Section 5 of the M-SIDH paper explains that hiding the degree adds no security, in the sense that one can reduce the problem to a case of known degree. Hence whatever is the security, it is coming from the fact that
is unknown to an attacker.
The reason why exact knowledge of the torsion is needed for the SIDH attacks is because these attacks set up an isogeny of Abelian varieties that is defined by an explicit kernel subgroup in terms of
and also the exact images of
under some other (known) isogeny. When given only
the kernel is wrong and the isogeny
is not the desired map (indeed, it may not even be an isogeny of polarized abelian varieties). So it was plausible that M-SIDH and FESTA might resist attack.
Castryck and Vercauteren show a more general attack strategy on these proposals than considered in the previous works. The paper builds on the well-known idea of “lollipops” (the terminology was introduced in this paper by de Quehen, Kutas, Leonardi, Martindale, Panny, Petit, and Stange). In isogeny crypto a lollipop is formed by taking an isogeny from one curve to another curve
, applying an endomorphism on
, and then applying the dual map back to the original curve
, so that the whole composition is cyclic. See the picture below from the paper linked above. Be warned that lollipops are not as sweet as they sound!
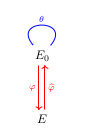
The obvious idea is to try to do a Kani-type attack on the isogeny , but this seems to be prevented by the blinding. The clever idea is to do Kani-type attack on a different isogeny
which uses the images of the blinded points
rather than the original points on
. The map
is a sort-of lollipop map with
, but one can also evaluate it (up to known scalar multiple) as the Frobenius map. Hence one can compute
. Knowing these points, one can mount the Kani-type attack and learn
.
We present one of the cases that is handled in the paper. Suppose that is defined over
. We have
and want to compute the unknown map
. Suppose that
is not defined over
. Consider the Frobenius maps
and
. Let
be the “pushforward” of the unknown map
, which is just the Frobenius conjugate of
. We have
. We don’t know
or
, but we can consider the composition, where
denotes the dual isogeny,
Note that the degree of is
. Further, we generally expect
to be cyclic, since for
we have
which is not usually equal to
.
The key result is Lemma 3 of the paper. Let . Let
, which an attacker can compute. The lemma shows that from these points one can determine
exactly. I emphasise the main point: the scalar multiplications by
somehow don’t matter, as we are directly attacking the points
. To finish the attack, one runs the previous SIDH attack on
, using Kani’s technique, to learn it completely. Finally, evaluate the isogeny on points of order
to learn
(since
is cyclic we can expect to learn the kernel we desire).
This gives an attack on M-SIDH when the starting curve is defined over
. The paper shows a more general attack that covers some more special cases of
. The general case of M-SIDH is not yet broken, but the paper discusses some strategies (and defenses) against a malicious party installing a backdoor in
.
The paper then studies a special case of FESTA, which is not proposed in the FESTA paper, and shows an attack. The paper says “FESTA with overstretched parameters is insecure”. But I believe no proposed case of FESTA is broken by this paper. The paper remarks that “similar information” is leaked in CSIDH, since maps the eigenspaces of Frobenius on
to the corresponding eigenspaces on
. However, there is no efficient attack known on CSIDH either. More generally, the information you get for free from an orientation does not seem to lead to any new attack.
While on the subject of CSIDH, these papers also do not break CSIDH:
- The supersingular Endomorphism Ring and One Endomorphism problems are equivalent by Aurel Page and Benjamin Wesolowski.
- The supersingular endomorphism ring problem given one endomorphism” by Arthur Herlédan Le Merdy and Benjamin Wesolowski.
Both papers are about knowledge of one endomorphism. The first shows that if one can generate one endomorphism for any random supersingular curve, then there is an efficient algorithm to compute the endomorphism ring (and hence solve isogeny problems) for any fixed supersingular curve. It sounds like this would break CSIDH, since in CSIDH we do know one endomorphism. But that’s not how the algorithm works. The idea is to take a target curve and generate random isogenous curves
, find an endomorphism on each curve
, and then pull these endomorphisms back to
. This then allows to compute
. But the one known endomorphism on every CSIDH curve does not allow to make this approach work. The second paper is about extending the known attacks on CSIDH to other curves, and it does not change the current understanding of the security of CSIDH.
What can we conclude from this about the security of fixes to SIDH, such as M-SIDH and FESTA? My personal opinion is that it seems unlikely that such simple tweaks to SIDH are enough to be secure. But I await more research to understand this better. On the other hand, CSIDH continues to withstand scrutiny by cryptanalysts, and no attacks are known that are better than the well-known subexponential-quantum-time Kuperberg algorithm.
— Steven Galbraith
